In today’s digital landscape, cyberattacks pose a significant and ever-growing threat to businesses worldwide. The evidence is clear: these attacks will remain a critical concern for the foreseeable future. While the methods and tactics of attackers continue to evolve, organizations can fortify their defenses by focusing on robust recovery strategies as a vital component of a comprehensive cyber resilience plan.
At the heart of any effective cyber recovery strategy lies the Isolated Recovery Environment (IRE)—a secure, standalone “clean room” environment. This space, completely disconnected from the production data center, serves as a safe haven for handling ransomware-infected workloads. Within the IRE, organizations can power on, inspect, and recover critical systems without risking further compromise, ensuring a clean and reliable restoration process.
By integrating an IRE into your cyber defense approach, your organization can enhance its ability to bounce back from even the most sophisticated attacks, safeguarding its future in an increasingly perilous digital world.
What is an IRE/Clean Room?
An Isolated Recovery Environment (IRE) is a dedicated, secure network space designed specifically for recovering from ransomware attacks. This “clean room” environment allows organizations to safely inspect, cleanse, and restore affected workloads without risking further contamination.
While building an on-premises IRE is an option, it often involves significant upfront costs. Companies must invest in infrastructure like backup appliances, servers, network hardware, and potentially even dedicated physical sites—not to mention the ongoing management expenses.
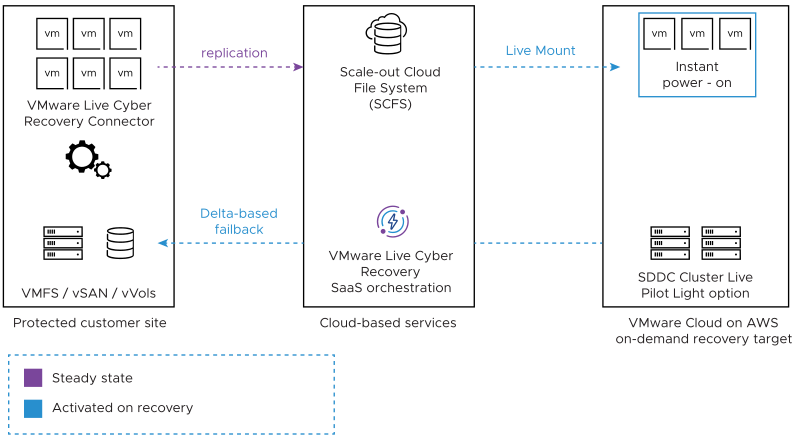
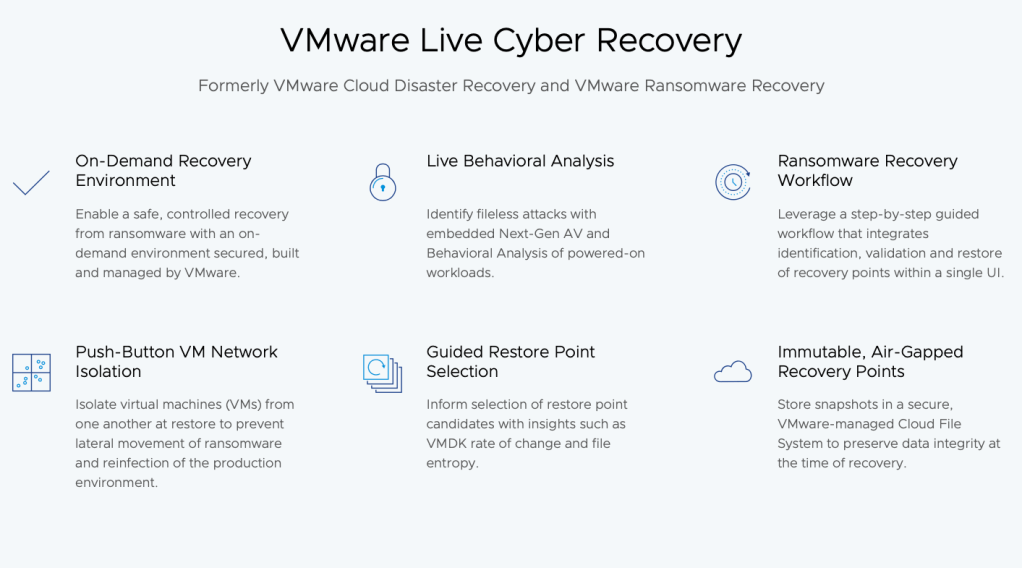
Enter VMware Live Cyber Recovery, which redefines the IRE by leveraging a VMware Cloud on AWS Software-Defined Data Center (SDDC). This cloud-based approach eliminates the need for costly physical infrastructure while simplifying deployment and management. With VMware’s Ransomware Recovery solution, businesses can quickly provision an on-demand IRE, resulting in faster recovery times, reduced operational risk, and streamlined complexity.
Key Features of a VMware-Based IRE:
- Secure Environment: A dedicated, cloud-based network where ransomware-infected virtual machines (VMs) can be safely powered on and assessed.
- Built-In Recovery Tools: Integrated resources for cyber response teams to verify, cleanse, and recover VM workloads efficiently.
- Rapid Recovery with Immutable Snapshots: Easy access to immutable backups ensures quick iteration through recovery points, speeding up the restoration process.
By transitioning to a cloud-based IRE with VMware, businesses can achieve a more cost-effective, flexible, and efficient cyber recovery strategy—ensuring resilience in the face of modern threats.
Environment Isolation
A defining feature of an Isolated Recovery Environment (IRE) is its isolation—a critical element for safeguarding the recovery process from ransomware attacks. This isolation ensures that the environment is self-contained and completely separated from production systems and external networks, creating a secure space for analyzing and restoring compromised workloads.
Traditionally, this concept is referred to as being air-gapped, meaning there is no direct network connection between the IRE, production systems, the internet, or any other internet-connected devices. This parallels the idea of a “clean room”in which virtual machines (VMs) are partitioned not only from external communication but also from one another. Access to and from the clean room is strictly controlled, and no data is allowed to leave unless it has been verified and cleaned.
How the IRE Works
The primary purpose of an IRE, or recovery SDDC, is to:
- Power on suspect workloads from a specific snapshot.
- Analyze behavior within a secure, controlled environment.
- Clean and stage workloads for safe recovery back into production.
To maintain the integrity of this process, the IRE is exclusively dedicated to recovery operations. It is not used for other purposes, such as testing, development, or temporary capacity expansion. Additionally, no user machines at the production site are permitted direct access to recovered VMs within the IRE.
By maintaining this level of strict isolation, an IRE ensures a secure, controlled recovery process, minimizing risks and accelerating the path back to operational stability.
Streamlining Cyber Recovery with VMware Cloud and NSX in an Isolated Recovery Environment (IRE)
A critical element of an Isolated Recovery Environment (IRE) is its secure and tightly controlled network edge. In VMware’s IRE design, the network edge is configured as an independent VMware Cloud Tier-1 Gateway, ensuring that all traffic to and from recovered workloads is routed exclusively through this gateway. This architecture prevents any connection between the IRE and production, testing, development, or QA environments. The only external connectivity allowed is to the internet, with strict NAT (Network Address Translation) applied to all traffic.
Simplifying Network Configuration
The isolated IRE setup allows recovered workloads to retain their original IP addresses by creating subnet segments attached to the Tier-1 Gateway. By leveraging NAT, organizations can reuse the same IP CIDRs for disaster recovery failover and IRE configurations without conflicts. This approach also ensures secure routing across different gateways during the recovery process.
During recovery, workloads remain within the boundaries of the IRE network, enabling safe inspection and repair. For advanced analysis, you can temporarily adjust a VM’s isolation level to observe suspicious behavior or test various network configurations without exposing production environments.
Leveraging VMware NSX for Cyber Recovery
VMware NSX is integral to the success of VMware Live Cyber Recovery by automating the creation and management of networking and security configurations. Key features include:
- Automated Firewall and Segmentation Rules: NSX generates artifacts prefixed with “CloudDR-Isolation-xx” to manage micro-segmentation and firewall rules, simplifying operations for users without advanced networking expertise.
- Dynamic Isolation Levels: These settings control VM access to resources such as the internet (for downloading patches) or to other workloads within the IRE. This flexibility supports behavioral analysis and validation before workloads are staged for recovery.
- Secure Quarantine Defaults: Recovered VMs are initially attached to a “Quarantine + Analysis” network rule, allowing limited outbound access to essential services (e.g., NTP, DNS, Carbon Black Cloud). This ensures integrated analysis tools like Carbon Black sensors function effectively while preventing unnecessary exposure.
Enforcing Secure Internet Access
For VMs requiring internet access during recovery, such as to download patches or security updates, traffic is strictly controlled via the NSX Advanced Firewall Gateway and NAT. No inbound internet access is allowed unless explicitly configured for specific testing purposes. To minimize risks, internet access for IRE workloads should always route through the VMware Cloud Gateway, avoiding any connection to the production environment.
Benefits of VMware Live Cyber Recovery
With VMware Live Cyber Recovery, organizations gain a streamlined, automated approach to managing network isolation and micro-segmentation within the IRE. Highlights include:
- Ease of Use: No advanced networking skills are needed, thanks to automated artifact creation and management.
- Integrated Tools: Built-in support for Carbon Black Cloud and other recovery tools enhances efficiency.
- Enhanced Security: Strict isolation policies reduce the risk of infected workloads impacting production environments.
By leveraging VMware Cloud and NSX, businesses can confidently manage ransomware recovery with greater efficiency, security, and control—protecting critical assets and reducing downtime.